Infra Play #120: CrowdStrike and the agentic era
What does the future of CrowdStrike look like in the era of AI?
The last two years have been transformational to the cloud infrastructure software landscape. Companies that didn’t even generate revenue before this period were able to accelerate to double or triple the ARR of some of the most established players in the industry. Capital has flooded the startup ecosystem in an unprecedented way, generating hundreds of companies trying to solve the same niche problem.
The explosion of software creation has had a profound impact in many ways, but cybersecurity remains the least discussed one. CrowdStrike is the most recognizable name in cybersecurity. There are very few individuals working in the industry who haven’t used, compared, worked for, or been impacted by CrowdStrike.
So when we ask what the future of CrowdStrike looks like, what we’re really asking is: what does cybersecurity look like in the agentic era?
The key takeaway
For tech sales and industry operators: Security is all about trust and the nice thing about trust is that it compounds faster than the pace of technology change. CrowdStrike has been able to expand significantly in recent years, driven by industry leading growth rates and strong platform expansion, based on both product adoption and a new consumption sales motion that reduces customer decision fatigue. The big bet in the coming years is that we will see an explosion of agentic use cases which will require new ways to secure your friendly agents and mitigate the impact from the adversarial ones. Essentially, cybersecurity will transition to a machine-to-machine model and they see themselves as the best positioned vendor to monetize the opportunity. Positioning here matters, since this thesis is not yet widely accepted in the industry and most customers are not thinking deeply enough about it. The obvious risks are related to quality of execution and timing, which means that being already positioned in the account and building trust early is critical. Their goal is to start “flattening the hiring curve”, so there isn’t a lot of time left to decide whether you want to be part of this directional bet.
For investors and founders: CrowdStrike sits at the intersection of three mega-trends: AI adoption, cybersecurity arms race escalation, and enterprise platform consolidation. This creates convex payoff characteristics: if their agentic thesis plays out, they will reach their $20B revenue target by FY36 (5x from current levels over 11 years), but their strong existing business provides downside protection through 80% gross margins and sticky customer relationships. The strategic insight is recognizing that agentic security isn’t just a product category but it will be driven by regulatory compliance. No regulated institution will deploy AI agents without compliance frameworks, and CrowdStrike is helping to write them. The biggest risk is if hyperscalers bundle security into core infrastructure (AWS/Azure/GCP all offer native security tools), turning cybersecurity into a feature rather than a product. CrowdStrike’s counter is the “trustworthy third party” positioning, i.e. enterprises want security vendors that aren’t also their cloud providers. For investors, the key question is execution timing: the “Agentic SOC” pivot needs to show adoption by 2026, or the entire thesis delays by 3to 5 years. If hyperscalers and frontier labs ship practical agentic security alternatives before CrowdStrike achieves category lock-in, they risk becoming expensive middleware rather than critical infrastructure. But if product velocity holds and regulatory capture succeeds, this becomes a $50B+ revenue opportunity with monopoly characteristics, the difference between a good cybersecurity company and a generational cloud infrastructure platform.
The only constant is speed
Source: Fal.Con event 2025
George Kurtz: I know everyone would be really disappointed if I didn’t start out with AI, right? It’s all here. Obviously, there’s lots of buzzwords that are out there, but I really want to dive into what it means for security and what it means for our opportunity. Mike, if you saw the keynote earlier, talked about speed, right? It was days and days and days of attacks. It became weeks. It became hours, minutes, seconds. At the end of the day, speed is the constant element.
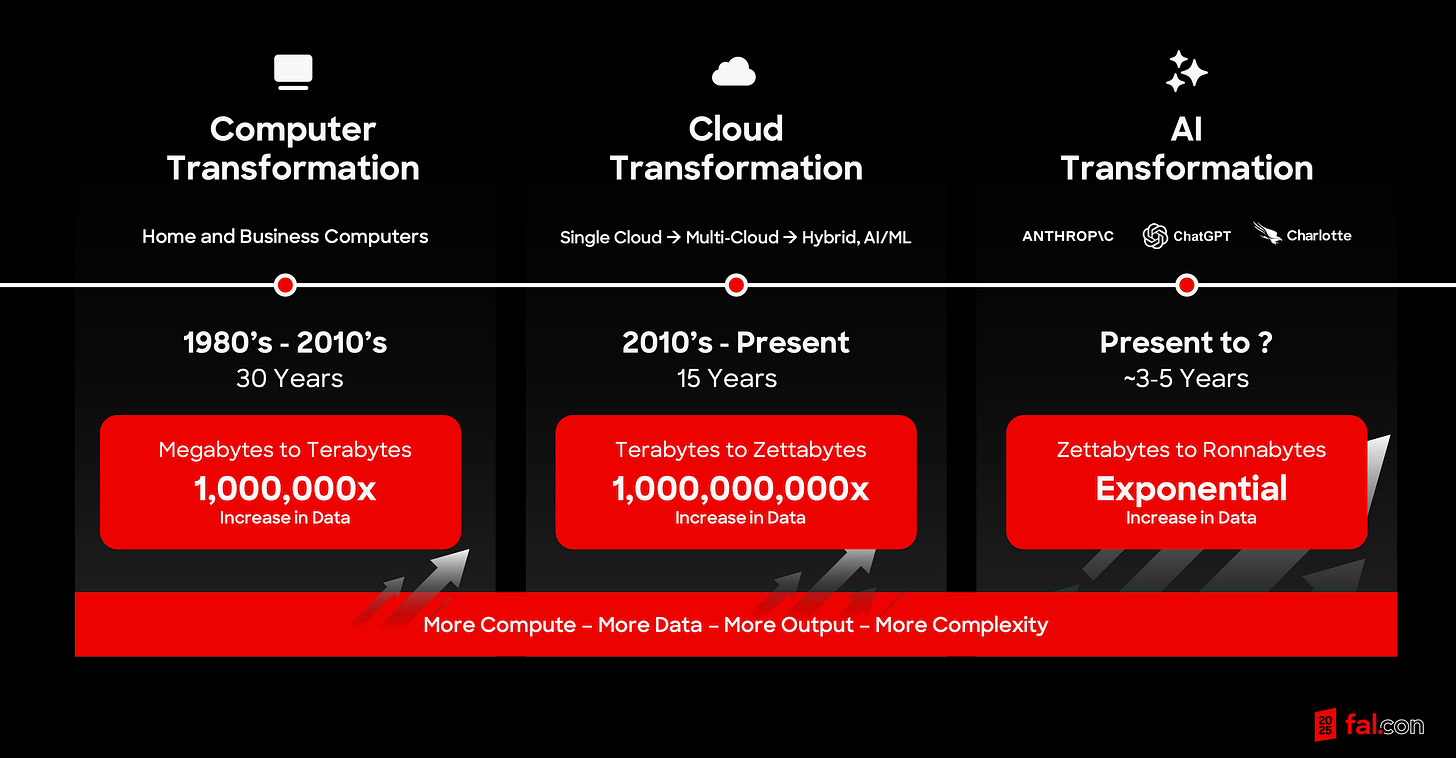
Let’s just kind of go through some of these transformations that we’ve had over the years. Some of you, like myself, who are probably old enough to remember this stuff, right?
1980s to 2010. It took 30 years for the computer transformation, the cloud transformation in 2010 to when I started the company to present, really 15 years. AI transformation, I think it was a really interesting stat. 100 million users of ChatGPT in just a couple of months after it was actually released. When we think about where the whole industry came from, right? It was megabytes to terabytes. It was terabytes to zettabytes. I have a new one for you. I think zettabytes to ronabytes. If you’ve heard of ronabytes, let me know. I had to look that one up myself, but it’s a million times bigger than the one before it.
Lots of scale that’s going on and AI really is transforming the world. We’ve seen all these mega deals happen. We see what’s going on with compute and obviously with GPUs.
One of the interesting conversations I had with some of the folks was really around sort of the lack of power that’s going to make all this work. All the chips in the world, all the security in the world, we still need the power to make all this actually work. For me, it really is about this transformation in data, a transformation in certainly opportunity for the adversaries to innovate as the earliest adopters. Some of the things that we’ve seen are incredible. Mike went through a few of the attacks.
One of them that I found really, really interesting just a couple of weeks ago that Adam’s teams found was one where there was a piece of malware. It landed on a system, and then it basically went back and did prompt after prompt after prompt to one of the GPTs, and it asked it, “Okay, what type of system am I on? What are the vulnerabilities? Where’s the data?” Write some PowerShell scripts to actually get the data and pull it together. Each system it landed on was a unique attack vector simply using prompts. It is just incredible how fast they’re working. If we think about cybersecurity’s first chapter, it was 30 years ago, and we’ll go through a couple of examples here. 2010 moves to the cloud, and obviously we’re in the AI era.
I remember these, I guess, like I said, unfortunately, fortunately enough, I remember all this stuff. Worms, I Love You virus, DDoS, Stuxnet, that all happened. It was weeks to days. Ransomware as a service. I thought one of the things that Mike talked about was really interesting in how ransomware moved from sort of as a service to now your AI models will actually optimize the revenue that you’re getting, that the bad guys are getting from each victim, which was really innovative but scary at the same time. Now we’re talking about really seconds, deep fakes. I had one bank call me just last week, and they said, “Hey, you know, our CEO is showing up in all these deep fakes.” It was a financial institution and was on crypto and all these sort of like fraudulent type things. How do we deal with all this?
We’re just at the tip of the iceberg in terms of what’s happening in AI. Obviously, it went from hours to seconds. As I said, things are moving very, very quickly. We’ve got to be there to be able to deal with these sort of challenges. What does tomorrow’s cybersecurity look like? What are we working on and delivering today for tomorrow? First, proactive. You’ve got to understand where the threats are. You’ve got to take an intelligence-led approach. You have to understand how the adversaries operate, and you have to meet them at the same speed. You also need to be surgical, right? Surgical in the fact that you have to be precise, right? It isn’t sort of blunt objects.
When businesses are running, they’re operating at a different speed as well, and you have to be able to meet them and deal with threats in real time and keep their business running. That’s a big part of it. This stuff can’t wait. It can’t wait days and weeks. You have to be there real time. A lot of the attacks that we’re dealing with, it’s not traditional malware. It’s not like you just find it and block it. These are very complex attack structures. We call them indicators of attack. They’re attack chains. We have to be able to put it all together in real time, both on the endpoints, in the cloud workloads, and in our own cloud to figure out if something bad is happening. We think this is best delivered in a single platform, right?
Let’s start with the obvious: CrowdStrike is a company that has been able to monetize fear and trust in every part of their go-to-market strategy. Even in this conversation, George introduces the challenges of today with a story based on fear, but this is something we can defend against if we have the right (platform) approach.
Keep reading with a 7-day free trial
Subscribe to Infra Play to keep reading this post and get 7 days of free access to the full post archives.